Product: ScreenOS
Version: 6.0 and higher
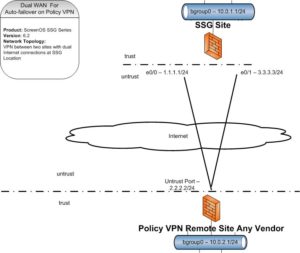
Network Topology
Two sites connected by VPN with one site having two internet access connections. They connect using policy based VPN.
Description:
This configuration has a redundant internet link on one side of a policy based vpn connection. The creation of two gateways and a group allows for failover between the two links and setting one as the priority link.
- Create a VPN Group
- Configure two gateways, one for each outbound interface
- Configure an AutoKey IKE for each of the gateways and select the VPN group designating the primary connection with the higher priority number.
- Configure the Policy using the VPN tunnel option and associate this with the VPN group
Configuration:
1. Create VPN Group:
This allows the two circuits connections to be treated as a single device to the VPN tunnel policy.
CLI
set vpn-group id 1
Web
VPNs – AutoKey Advanced – VPN Groups
New
2. Configure two Gateways
Create a gateway for each of the two outbound interfaces
CLI
set ike gateway Primary-GW address 2.2.2.2 Main outgoing-interface “ethernet0/0” preshare Juniper== sec-level standard
set ike gateway Backup-GW address 2.2.2.2 Main outgoing-interface “ethernet0/1” preshare Juniper== sec-level standard
Web
VPNs – AutoKey Advanced – Gateway
New and select the correct interface for each on the advanced page
3. Configure AutoKey IKE
Create IPSEC object on each gateway and place into group
CLI
set vpn RemotePrimary gateway Primary-GW no-replay tunnel idletime 0 sec-level standard
set vpn-group id 1 vpn RemotePrimary weight 10
set vpn RemoteSecondary gateway Primary-GW no-replay tunnel idletime 0 sec-level standard
set vpn-group id 1 vpn RemoteSecondary weight 1
Web
VPNs – AutoKey IKE
New select the correct gateway on the opening page
select the group on the advanced tab and set priority (higher is Primary)
4. Configure Policy Tunnel
The tunnel will associate with the group and can use either circuit connection but will prefer the higher priority one first.
CLI
set address Trust LocalLAN 10.0.1.0 255.255.255.0
set address Untrust RemoteLAN 10.0.2.0 255.255.255.0
set policy name RemoteVPN from Untrust to Trust LocalLAN ClinicLAN ANY tunnel vpn-group 1
set policy name RemoteVPN from Trust to Untrust LocalLAN RemoteLAN ANY tunnel vpn-group 1
Web
Policies – Policy Objects – Addresses – List
Create Remote LAN address in Untrust zone
Create Local LAN address in trust zone
Policies – Policy
Create trust to untrust policy and check the box to create a matching policy
Select tunnel and select the VPN group
Verification:
Confirm SA is up
CLI
get sa
Web
VPNs – Monitor Status
Disconnect the primary ethernet cable and confirm the failover occurs
References:
ScreenOS Concepts and Examples Guide
http://www.juniper.net/techpubs/software/screenos/screenos6.2.0/index.html
Route based VPN tunnels
Concepts & Examples Guide
Volume 5 Virtual Private Networks
Chapter 3 VPN Guidelines
Chapter 4 VPN: Sit-to-site VPN Configurations
Originally Posted June 04, 2011
Last Revised on June 04, 2011
Hi Steve, I found this post https://forums.juniper.net/ and I was wondering if you can offer any insight or a doc that can help me. We have a Cisco ASA that has two one Gig circuits from two ISP’s. The Primary Circuit has an IPSec tunnel from ASA to a Juniper SSG5 and it works. What I want to do now is build a second tunnel from the second Circuit on the ASA to the Juniper and have it pass traffic only if the Primary ISP is down. So in effect, Primary ISP down, we can still access subnet behind Juniper when up on Secondary ISP circuit. I know the ASA but I do not have a grasp of the SSG5. I attempted this once and took down the Primary Tunnel. Any help you can offer would be greatly appreciated.
Best Regards,
Jerry Roy
jroy@remotehand.com
It sounds like this is the configuration you are looking for which fails vpn over between two different local gateways to the same remote gateway address.
Steve